Security
-

What is an SSL Certificate? Why is it Needed
A tool such as an SSL certificate allows you to exclude the unauthorized transfer of personal data to third parties.…
Read More » -

Rethinking Security: Why Passwordless Authentication Is the Future
Tradition means passwords and login will be obsolete soon. The need to eliminate passwords in logins has come to an…
Read More » -

8 Internet Safety Rules for Safe Internet Use
We all use the internet and several online activities like using social media sites, playing online games, getting information from…
Read More » -

5 Reasons for an SSL Certificate For Your Website
People are online more than ever because of the latest mobile technology and high internet speeds. They visit different websites…
Read More » -

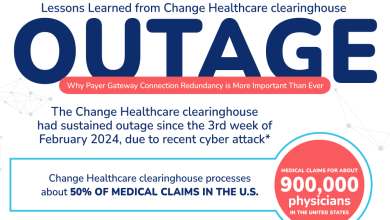
Fighting Cyber Attacks With Redundant Payer Systems
The Change Healthcare clearinghouse is one of the nation’s largest clearinghouses, responsible for processing nearly 50% of medical claims in…
Read More » -

Enhancing Cybersecurity – Real-World Examples of SOC Automation in Action
Digital landscapes undergo swift transformations daily. Today, cybersecurity is a big concern across various organizations. Each needs a strong security…
Read More » -

Is Cyber Security Hard? Understanding the Challenges and Rewards
Cybersecurity is a crucial and evolving field of study in today`s digital world. As technology advances, cyber attacks and cyber…
Read More » -

Cryptocurrency and Cybersecurity: Protecting Your Digital Assets from Threats
Over the years, cryptocurrency has become very popular. However, with this huge digital asset rush, there is a need for…
Read More » -

How to Protect Your Digital Identity – A Complete Guide
In this digital world, most of our existence is wrapped up in the online world. Whether paying bills, buying groceries,…
Read More » -

A Guide on How to Protect Your Personal Data Online
As you can imagine, online data protection has never been more important. The more we use the internet for business,…
Read More » -

Maximize Cybersecurity Practices For Businesses – Learn How
Small and medium-sized enterprises (SMBs) must have a plan in place to protect their online privacy as the digital world…
Read More » -

How To Manage Cybersecurity Attacks As An iGaming Business?
Some of the biggest companies in the world have only as strong of cybersecurity as their most vulnerable line of…
Read More » -

Top 10 Practices for Maintaining a Secure Server
Maintaining a secure server is vital as it plays a huge role in maintaining data privacy and ensuring the integrity…
Read More »