Why Attack Surface Management Is the New Black in Cybersecurity

Every business wants to grow, but growth comes at a price. When a company expands its online presence, it increases the risk of cyber attacks. That happens simply because a growing company starts to have more external-facing assets with their respective vulnerabilities, more employees (that can accidentally expose something), more devices, misconfigurations, and other potential causes of cybersecurity issues.
The only way to prevent the likelihood of cyberattacks from increasing is to adopt the right security measures. Attack surface management (ASM) is one of the most popular cybersecurity approaches right now, with its popularity continuing to increase. Fortune Business Insights predicts that the attack surface management market will continue to grow at a pace of 22.3% per year, indicating that more and more companies turn to this technology for protection.
In this article, I will explore attack surface management as a concept, give some perspective on its popularity, and provide recommendations on how you can choose the best ASM solution.
Let’s start with definitions!
What Is an Attack Surface?
An organization’s attack surface contains all its digital and physical assets together with their respective vulnerabilities. In other words, an attack surface is a sum of all attack vectors that can be used to get unauthorized access to the organization’s systems.
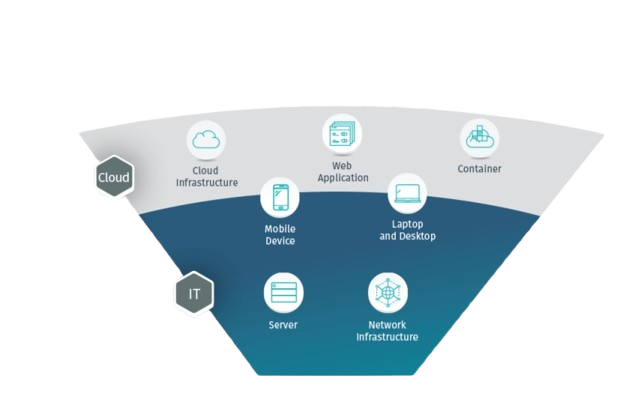
An organization’s attack surface includes:
- Applications (web, computer, mobile – all of those);
- Websites (together with 3rd party technology used on them);
- Networks (including cloud networks and virtual private networks);
- Devices (from smartphones and computers to IoT and servers);
- Cloud infrastructure.
What Is Attack Surface Management?
Attack surface management is the continuous process of identifying, prioritizing, remediating, and monitoring the new attack vectors that add to the organization’s attack surface.
Attack surface management fulfills its main objective through rapid reduction of organizational attack surfaces by addressing the most harmful available entry points. ASM uses proactive tactics to provide an attacker’s simulated perspective which enables identification of security weaknesses throughout the entire system.
ASM extends its security protection from digital risks to physical dangers as well as social engineering issues including insider threats and phishing attempts. Offensive-minded approaches help organizations detect developing threats early so they reduce their exposure to attacks.
Why Is Attack Surface Management Important (and So Popular)?
Attack surface management is becoming increasingly popular among businesses of different sizes because ASM tools help address the problems that traditional cybersecurity solutions struggle with. Below are a few reasons why ASM is so attractive to businesses nowadays:

1. A Hacker’s Perspective
An important part of ASM is EASM, external attack surface management, that only considers internet-facing assets, but does so from an attacker’s perspective. Since EASM tools see the organization’s attack surface the same way a threat actor does, it becomes much easier for cybersecurity teams to identify, prioritize, and remediate issues that are the most likely to lead to a successful cyberattack.
2. Expanding Digital Footprint
Cloud adoption, remote work, and third-party integrations have dramatically increased the number of exposed assets, making continuous monitoring essential, yet difficult. Traditional cybersecurity tools such as antiviruses and firewalls don’t extend to the cloud and struggle to cover the entire attack surface. ASM covers it all.
3. Evolving Cyber Threats
Attackers leverage modern technology just like everybody else does. They are increasingly using AI-driven techniques, supply chain compromises, and sophisticated social engineering tactics. Addressing all of that requires a proactive security approach like the one that ASM takes.
4. Regulatory Pressures
Data privacy regulations such as GDPR and standards such as PCI DSS require organizations to promptly address vulnerabilities in their systems. That means that vulnerabilities have to be discovered, prioritized, and remediated in time. ASM tools help do exactly that and they continuously monitor for those vulnerabilities, which makes more and more organizations adopt ASM to meet regulations and industry standards.
5. Rising Cyber Insurance Costs
In many industries, cyber insurance has become if not mandatory, then highly recommended by regulators. Each year, insurers are demanding stronger security measures, and ASM helps organizations demonstrate effective risk management.
Benefits of Using Attack Surface Management Tools
Let’s take a look at the benefits of using attack surface management tools:
1. Continuous Visibility Into the Organization’s Attack Surface
ASM offers real-time insights into an organization’s entire attack surface, including shadow IT, third-party risks, and newly exposed assets. This prevents blind spots that attackers might exploit. As the organization grows, ASM discovers more of its assets and helps protect them in a timely manner.
2. Risk-Based Prioritization
By assessing vulnerabilities from an attacker’s perspective, ASM helps security teams focus on the most critical threats, reducing noise and improving response efficiency. Advanced attack surface management tools consider factors such as exploitability, asset business criticality, likelihood of threat actors using a certain attack vector, and more.
3. Proactive Threat Mitigation
Rather than reacting to incidents after they occur, ASM enables organizations to identify and remediate vulnerabilities before they can be exploited, minimizing potential damage. In cybersecurity, prevention is always better than reactive response.
4. Reduced Manual Effort
Cybersecurity teams are almost always understuffed, so it is important to reduce the manual effort as much as possible. That’s why cybersecurity increasingly relies on automation, and ASM tools help reduce the workload on your IT and security teams by partially automating vulnerability management – from asset inventory to vulnerability discovery and from streamlining remediation to continuous monitoring.
5. Cost Savings
Cybersecurity is often considered an expense rather than something that generates value, but you can look at it from a different perspective – ASM tools help cut down the costs because they prevent costly downtime and save a lot of money in the long run.
How to Choose The Right External Attack Surface Management Vendor?

Well, there is no tool that is the best for every business, but I’ll provide a list of parameters that you need to consider when choosing an attack surface management tool.
1. Comprehensive ASM Capabilities
The platform should cover asset discovery, vulnerability scanning, prioritization, remediation, and continuous monitoring. Look for broad asset discovery, accurate scanning with minimal false positives, flexible prioritization options, and remediation features like ticketing integrations or automated fixes.
2. Effective Continuous Monitoring
Some vendors define “continuous” in “continuous monitoring” as weekly scans, while others trigger scans based on new threats or provide real-time detection. Choose a platform that offers real-time or event-driven scanning and possibly allows different scan frequencies for different asset types.
3. Scalability & Pricing Transparency
Attack surface management can cost you anything between USD $100/month and $10,000/month or even more. Vendors charge based on attack surface size, but pricing models vary widely. Some provide clear public pricing, while others require negotiations. The most important thing is to ensure that the platform scales with your infrastructure and doesn’t consume your entire cybersecurity budget if the company grows (and the budget doesn’t).
4. Ease of Use & Support
Some ASM platforms require complex setup, while others are more user-friendly. Consider deployment requirements and time to value, built-in compliance reporting, and the quality of customer support, including response times, onboarding assistance, and documentation.
Conclusion
Businesses now consider Attack Surface Management (ASM) as their vital cybersecurity method because digital environments increase complexity alongside rising threats.
Businesses that expand their digital footprint through online platforms face a struggle from traditional security measures which leads them to adopt ASM because it provides real-time risk insights and threat mitigation capabilities. Businesses across multiple sectors and all organizational scales should make this essential investment because it enables effective attacker simulation along with automated vulnerability control and regulatory compliance.
Companies need to evaluate ASM services based on their capabilities along with scalability options and frequency of monitoring as well as integration compatibility and affordable rates. While no single solution fits every organization, the key is to find a platform that aligns with your security needs, provides actionable insights, and enhances overall risk management.




