Remote Desktop Security Settings – How to Secure RDP?

Remote Desktop Protocol (RDP) is a fundamentally secure protocol, but vulnerabilities such as weak passwords, disabled Network Level Authentication (NLA), and unpatched system can compromise its safety.
It’s natural to be concerned about Remote Desktop Security. Without proper protection, RDP can expose your system to data breaches, malware, and even full server takeover by hackers.
If you do not know how to secure remote desktop, you are in the right place. This post covers all the necessary solutions to secure RDP. However, if you want to overcome personal system limitations and start your work at a high level of security, using an RDP server is an optimal approach.
You can combine security solutions like using 2FA authentication and limiting user permissions with the default security provided by the RDP server. In this case, you become an unreachable target for hackers who are one step ahead of any threat.
Is RDP Secure?
RDP is a protocol developed by Microsoft that has security features and 128-bit encryption by default. However, answering this question with a definite “no” or “yes” is incorrect. The security level of RDP connections depends on how you configure the settings and use RDP.
Weak login credentials, use of the default port, and outdated software are some of the vulnerabilities that require manual implementation of related solutions.
However, vulnerabilities such as malware execution, unauthorized traffic, and connection disruptions due to DDoS attacks are addressed by default using a secure RDP.
If you buy cheap RDP from a reputable provider, you will save money and benefit from advanced security measures such as DDoS Protection and advanced firewalls, which play an important role in secure remote desktop.
Also, with root access to this RDP, you can freely implement security solutions to enhance your remote connections without limitations.
Top 12 Remote Desktop Security Tips to Maximize Protection
Implementing the following measures will significantly boost your RDP security and allow you to focus on your core tasks with peace of mind.
1. Use Strong and Unique Passwords
The remote desktop login page is the first defense against unauthorized access. Use complex passwords to make the remote system resistant to brute force attacks.
Here are a few essential tips for creating strong passwords:
- The password length should be more than 10 characters.
- Use a combination of uppercase and lowercase letters, numbers, and special characters.
- Avoid using common words or easily guessed information
- Use unique and independent passwords for each account.
- Use a password manager to create and manage passwords more securely.
Passwords from professional RDP providers usually follow strong security standards, but to maintain a high level of protection, they must be updated every 3 to 6 months and avoid reusing old passwords.

2. Implement Multi-Factor Authentication (MFA)
The more complex the RDP login process, the less likely it is to be compromised. Therefore, create additional layers of security with MFA so that even if your password is compromised, it is still impossible to access the system.
Authenticator tools, certificate-based smartcards, and biometric verification are standard solutions for Multi-Factor Authentication.
Enabling MFA may make the authentication process more time-consuming for you, but when it comes to remote desktop security, a few seconds of delay is worth protecting sensitive data and preventing hackers from intruding.
3. Enable Network Level Authentication (NLA)
Microsoft provides NLA, a security solution that requires users to authenticate before creating a session (full desktop load). This provides an additional security layer and prevents unauthorized users from consuming server resources.
NLA is enabled by default in Windows 10 and Windows Server 2012 R2/2016/2019. However, to ensure that it is enabled, check the following path in Group Policy:
Computer\Policies\Windows Components\Remote Desktop Services\Remote Desktop Session Host\Security
In this path, the option “Require user authentication for remote connections by using Network-Level Authentication” must be enabled.
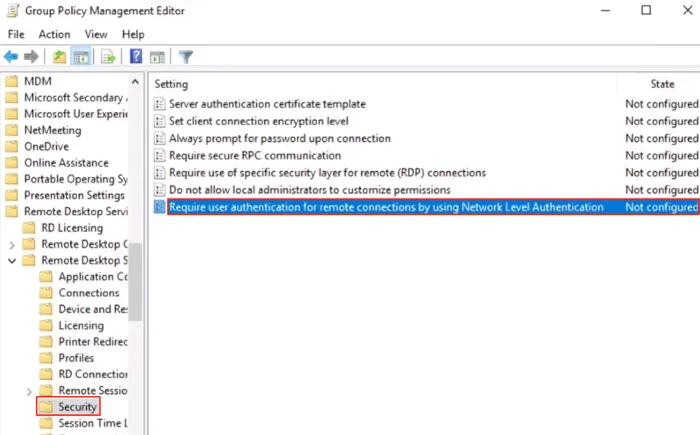
This feature must also be enabled on the RDP server running the Remote Desktop Session Host role.
Combining NLA with DDoS Protection provided by cheap RDP ensures that high traffic and simultaneous attacks will not disrupt or slow down your server.
4. Restrict RDP Access
By restricting access to the remote device, you can create fewer, more controlled entry points, which enhances RDP security and reduces the risk of unauthorized access from unknown IPs or users.
Here are several effective methods to achieve this:
- Use IP Whitelisting to allow connections from specific IP addresses.
- Remove local administrator accounts from RDP access.
- Create a dedicated group for RDP users and restrict its membership.
- Remove all admin accounts if you are not using RDP to manage the server.
- Restrict RDP access to specific hours of the day.
These security settings should be made on the RDP server to increase RDP security. If you buy cheap RDP server with root access, you will not be restricted in performing these operations.
5. Change the Default RDP Port
RDP uses port 3389 by default, which makes it a common target for automated attacks and network scanners. Therefore, changing it to a custom port is an effective way to enhance RDP security.
Select a unique and unpredictable port number, and ensure it is open in the firewall to prevent connection issues and avoid locking the RDP server.
To do this, simply follow these steps:
1. Open the Registry Editor using the Search box.
2. Navigate here:
HKEY_LOCAL_MACHINE > System > CurrentControlSet > Control > Terminal Server > WinStations > RDP-Tcp
3. Scroll down and find PortNumber and then double click on it.
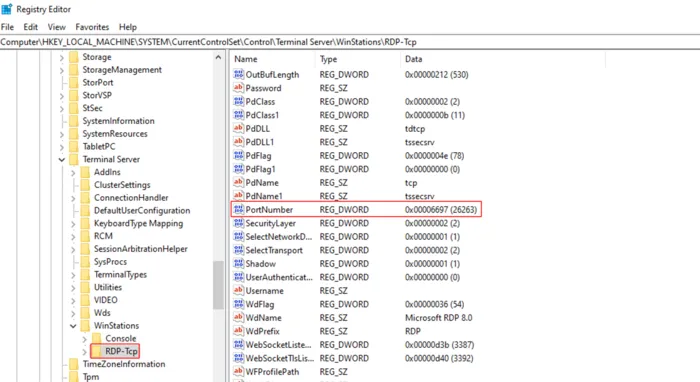
4. Replace 3389 with your desired port number and save it.
It is a good idea to monitor RDP port access attempts periodically and change it if necessary.
6. Enable Firewall Protection for RDP Security
A firewall acts as a gateway that controls incoming and outgoing connections based on defined rules. With proper firewall protection, you can effectively manage and secure RDP connections.
Whitelisting IPs, blocking unused ports, and restricting traffic by region are key firewall rules to boost remote desktop security.
Implementing a hardware firewall is another strong way to secure remote desktops. It can enhance your security setup with features like IDS, IPS, and app-level filtering that give you granular control over all network traffic.
If you buy cheap RDP that is equipped with advanced firewalls, filtering suspicious traffic and controlling access will certainly be performed with higher quality, which guarantees a secure remote desktop and prevents possible intrusions.
7. Use a VPN for Secure RDP Access
A VPN creates encrypted shields around remote connections that ensure secure remote access.
Stay anonymous online with VPN, hide your IP addresses, and encrypt your data before you connect to the RDP server. Encrypting and authenticating communications adds an extra layer of security, making it harder for unauthorized parties to intercept sensitive data.
To set up a VPN for RDP, you need to:
- Choose a trusted VPN service.
- Set up and configure the VPN on the RDP client and server.
- Before starting the RDP session, connect both devices to the VPN.
8. Keep Your System Updated
Software vulnerabilities are discovered over time and fixed in updates. Regularly updating your system helps prevent hackers from exploiting these vulnerabilities.
The operating system, drivers, applications, remote desktop clients, VPNs, multi-factor authentication tools, and firewalls are some critical components that should be updated regularly.
You can enable Microsoft’s automatic updates to ensure that your operating system and RDP client are always up-to-date. But it’s better to check regularly and update manually if necessary.

9. Limit User Permissions and Access Rights
If multiple users have access to the RDP server, try to set each user’s access to the minimum privileges necessary to perform their role.
This limits users’ access to essential resources, so even if a hacker breaches one account, their actions are restricted, and they can’t access sensitive parts or critical data.
You can set access through Group Policy or Role-based Access Control. If you buy RDP server, your connections’ overall security will increase, and you will also have complete operational freedom to implement detailed and professional security policies.
10. Limit login attempts
Brute force attacks try various username and password combinations to access RDP. To protect against this, you can set a policy that locks the account after several failed login attempts.
To configure this policy, open the Group Policy Editor and navigate to:
Computer Configuration > Windows Setting > Security Setting > Account Policies > Account Lockout Policies
Set the desired values for the following options:

Account lockout duration: The amount of time an account remains locked after reaching the failed login limit.
Account lockout threshold: The number of failed login attempts allowed before the account is locked.
Allow Administrator account lockout: Determines whether the Administrator account can be locked after failed login attempts.
Reset account lockout counter after: The period after which the failed login attempt counter resets if no additional failed attempts occur.
11. Use RDP Gateways
RDP Gateway acts as an intermediary between the client and the RDP server. Instead of establishing a direct and insecure remote connection, RDP Gateway tunnels the connection to a secure port (HTTPS) using SSL encryption.
In this way, RDP traffic is first transmitted to the Gateway server and then redirected to its final destination. This process keeps RDP traffic hidden from external attacks and helps secure the network.
You must install the Remote Desktop Services and Remote Desktop Gateway roles using server manager to deploy the Gateway.
Then, use the RD Gateway manager to configure the SSL Certificate, set up RD CAP and RD RAP, and configure network settings such as opening port 443 on the server.
After performing these operations, to establish a connection with the remote system, you must enter the Gateway server address in the RDP client settings so that client traffic is manually redirected to the RD Gateway server.
12. Monitor and Log RDP Activity
Reviewing logs of RDP attempts and activities regularly is an excellent strategy for maintaining RDP security. This allows you to identify and prevent suspicious behavior, unauthorized access attempts, and high resource usage on time.
The RDP server provider also offers advanced logging features and tools to help you do this more efficiently.
To speed up your monitoring, you can set up automatic alerts for unusual activity, such as repeated failed login attempts or access from IP addresses.
Overview of RDP Security Methods
| Security Method | Risk Prevented | Implementation Effort | Cost / Tools Needed | Recommended For |
|---|---|---|---|---|
| Strong & Unique Passwords | Brute force attacks | Low | Free – Use of password manager | All users |
| Multi-Factor Authentication | Password leakage, credential theft | Medium | Authenticator apps or hardware tokens | Businesses with sensitive data or public servers |
| Network Level Authentication | Unauthorized session creation | Low | Free – Built into Windows | All Windows Server users |
| Restrict RDP Access | Access from unknown or malicious IPs | Medium | Free – Configured via Windows Firewall | Businesses with fixed IPs or internal networks |
| Change Default RDP Port | Port scanning, automated bot attacks | Medium | Free – Manual registry edit | Small to medium businesses |
| Firewall Protection | Unauthorized incoming/outgoing traffic | High | Built-in Windows Firewall or third-party firewall | All setups |
| VPN for RDP Access | IP exposure, data interception | Medium | VPN subscription | Remote teams, freelancers, and organizations |
| System Updates | Exploitation of known vulnerabilities | Low | Free – Use Windows Update | All users |
| Limit User Permissions | Full hacker access | Medium | Free – Managed through Group Policy | Multi-user environments |
| Limit Login Attempts | Brute force login attacks | Low | Free – Configurable via Group Policy | All users |
| Use RDP Gateway | Direct exposure of RDP server | High | Windows Server license, SSL certificate, and setup expertise | Enterprises with large remote workforces |
| Monitor RDP Activity | Delayed detection of threats or intrusions | Medium | Event Viewer, Windows Logs, or professional tools | Multi-user environments |
What are the Main RDP Security Vulnerabilities?
Given the simplicity and efficiency of data transmission via RDP, it becomes an attractive target for attackers if not properly secured. Any vulnerabilities in the protocol can come with their associated risks, all of which are dangerous.

The risks that may occur without securing RDP are as follows:
Easy access to user accounts with brute force attacks:
Weak authentication mechanisms, such as easily guessable passwords or lack of multi-factor authentication (MFA), enable attackers to try multiple login credentials and ultimately gain unauthorized access to user accounts.
Execution of malicious code remotely and control the system:
Outdated versions of RDP or software introduce vulnerabilities in the protocol that attackers can exploit to remotely execute malicious code and gain complete control of the system.
Exploitation or theft of sensitive information:
Without encryption in RDP sessions, transmitted data becomes vulnerable to interception, enabling attackers to capture and steal sensitive information, such as login credentials or confidential business data, during remote access.
Server disruption due to high traffic volume:
When RDP servers lack DDoS protection, they become susceptible to traffic-based attacks that consume resources, disrupt normal operations, and prevent legitimate users from establishing connections.
Direct and unfiltered access by hackers to the RDP server:
Exposing RDP directly to the internet without a VPN or RD Gateway removes critical security barriers. This allows attackers to scan, identify, and connect to the server with minimal resistance, increasing the risk of unauthorized access and targeted attacks.
Execution of malware such as Ransomware or Trojans on the server:
Malicious activities such as ransomware or Trojans can spread without continuous system monitoring or detection of unusual behavior, giving attackers enough time to spread throughout the system and cause serious damage.
Using RDP as a tunnel to infiltrate internal networks:
Improper firewall configurations, such as leaving RDP ports open or inadequately filtered, provide attackers with an entry point that can tunnel into internal networks and launch further attacks on other systems or resources within the organization.
These risks can lead to unauthorized access to sensitive data and resources within seconds, which can cause financial loss, loss of organizational reputation, or damage to confidential information.
If you buy Cheap RDP, you get advanced security measures for a reasonable price that eliminate most of these risks. Then, using root access, you can take steps to eliminate other risks.
Remote Desktop Protocol (RDP) Alternatives
RDP is a proprietary Microsoft protocol that connects to Windows systems. However, other solutions can establish these connections with their protocols.
To choose the right remote desktop solution for business, consider essential points such as compatibility, required features and performance, price, maintenance costs, technical support, and scalability.
TeamViewer, AnyDesk, ISL Online, and Splashtop are best remote desktop software for establishing secure and fast remote connections to different systems.
Most of these software offer features beyond simple remote connections, and the right choice among these tools depends on your specific business needs, scalability, and budget.
Conclusion
Securing your RDP connections is crucial to preventing unauthorized access and malware. You can boost security using strong passwords, multi-factor authentication, and firewalls. Investing in a reliable and cheap RDP provider with advanced security ensures safe remote work.




