Cyber Threat Hunting- Complete Guide

In the process of cybersecurity nowadays, cyber threat hunting is an important component of a security operation center (SOC). With cyber threats getting more and more complicated and dynamic by the moment, this shows the disadvantages of a passive defense approach.
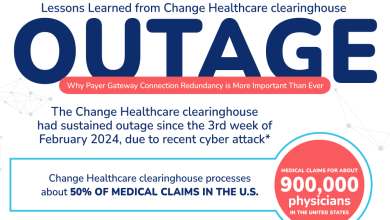
According to a Cybersecurity Ventures report, the cost of cybercrime reached $8 trillion in 2023 and is projected to rise to $10.5 trillion by 2025. This is the reason, organizations are integrating cyber threat hunting into their cybersecurity strategies to reduce attacks.
The approach is more than just reactive. It is a strategic move towards detecting and preventing the possible risks. Cyber threat hunting is driven by a systematic and proactive approach that involves the detection of threats within the organization’s digital environment.
Unlike conventional security methods which are utilizing predefined signatures or patterns, threat hunting employs analysts’ expertise and thorough examination of the networks, systems, and datasets looking for indications of malicious activities.
By being proactive, the security teams can ensure that the threat is well controlled and eliminated before it develops into major security incidents.
In this blog post, we will learn what is cyber threat hunting and how it is transforming the cybersecurity secotr.
Let’s start here!
Introduction to Cyber Threat Hunting
Cybersecurity, with its constant transformations, has no other option but to always be at least one step ahead of the threats. With the purpose of being pre-emptive, cyber threat hunting is a process of professionals known as dedicated security analysts who research all networks, systems, and datasets for some malicious activities that slipped away the existing security measures.
Different from automated security solutions relying on predefined threat signatures, threat hunting application is a more competent one which uses the best detection tools available in the market as well as the knowledge of security experts who can spot even unknown threats.

The Critical Need for Threat Hunting
The capability of more intelligent and refined cyberattacks to raid through automatic defense mechanisms becomes more and more evident. These systems, although necessary, are incapable of detecting advanced threats.
The actions of the threat hunter will fill a targeting hole to investigate the attacker’s TTPs and IOCs that reveal the attack. The proactive method not only looks for potential threats but also dissuades the escalation to major security situations.
Role of Cyber Threat Hunting in Modern Security Operations
Cyberspace is now ruled by cyber threat hunting, which is a perfect part of regular security operations. As companies try to overcome the increasing variety and sophistication of cybersecurity threats, the imperfections of the historical reactive model become obvious. Organizations after the cyber threat hunting will move towards an active strategy to get to the point of forewarning and preventing risks.
At the heart of cyber threat hunting is a systematic and proactive technique of uncovering the threats existing among the organization’s digital assets. Unlike the traditional security methods, which are signature-based, threat hunting utilizes the skill set of expert security analysts to minutely and diligently inspect networks, systems, and datasets for traces of bad activities. This benign approach helps security teams to prevent threats from developing into dangerously big security breaches.
Besides, cyber threat hunting is the principle of continuous and adaptive development. Security analysts are utilizing a mix of threat intelligence, behavioral analysis, endpoint detection and response (EDR) solutions and security information and event management (SIEM) systems to refine their hunting strategies and overcome the appearing threats.
At its essence, cyber threat hunting reflects a paradigm change in cyber security operations enabling businesses to move from passive to active cyberspace defense. By adopting this preventive strategy, businesses can strengthen their security stance and lessen the opportunities for attacks by hackers.
Techniques and Tools Used in Threat Hunting
Here are the most useful techniques and tools in threat hunting:
Hypothesis-Driven Investigation
The foundation of threat hunting lies in formulating a hypothesis based on threat intelligence, recent security incidents, and anomalies detected by security tools. This hypothesis steers the threat hunters in their search for evidence of malicious behavior, guiding their exploration through the vast amounts of data within an organization’s digital environment.
Behavioral Analytics
Attackers often use decoys to mask their activity. By performing behavioral analysis, they can identify the enemies well so as to detect any unusual behavior within the networks. The big data analysis tools that filter through the information in order to identify such anomalies from which possible threats could be detected early have a very important role to play in this process.
Endpoint Detection and Response (EDR)
EDR solutions provide a detailed view into endpoint activities, for example, process executions, network connections, and file operations. This degree of precision is particularly required to explore and decipher the minutia of possible threats which makes EDR a key element of the hunter’s armory.
Threat Intelligence Platforms
Keeping abreast of new threats and assail techniques for applicable hunting is imperative. Threat intelligence platforms gather information from a host of sources, and the hunters get to have the most updated intelligence on today’s cyber threats.
Security Information and Event Management (SIEM)
The SIEM is the center of threat hunting as it correlates and analyzes the data sourced from multiple locations in the corporation. This allows events to be tied together with the recognition of patterns which might indicate a breach and help in the early detection of danger.
Exploring Threat Hunting Capabilities with DigitalXraid
Selecting the right partner for enhancing an organization’s threat hunting capabilities is critical. DigitalXraid stands out with its CREST-accredited Security Operations Centre (SOC), offering SOC as a service. This arrangement provides organizations with the necessary skills and technology for effective threat hunting. The arm of experts of DigitalXraid uses the latest technology to detect, investigate, and remedy any possible cybercrime threats, assuring the security of digital assets.
Final Thoughts
Threat hunting is a key preventive security measure, which allows organizations to identify and neutralize dangers before they do damage. With the use of different strategies and devices such as hypothesis-driven investigation and EDR and SIEM systems, firms can skyrocket their security level.
Reliable threat-hunting services empower organizations by providing expert support and technology, making advanced threat-hunting accessible and effective. In the dynamic field of cybersecurity, embracing threat hunting is a strategic move towards safeguarding an organization’s data, reputation, and operational integrity.